New on LowEndTalk? Please Register and read our Community Rules.
All new Registrations are manually reviewed and approved, so a short delay after registration may occur before your account becomes active.
All new Registrations are manually reviewed and approved, so a short delay after registration may occur before your account becomes active.

















Comments
thx for your understand, i don't think anyone will test their server by ddos, even the provider not mention about what protection they have...
if provider say i am trying spoof and ddos other server, ok, it is possible.but trying to ddos my own server? lol, this isn't the ovh...
hope they can find out the reason, or just let me out
As long as there are no further DoS attacks against your server, then we'll have no problems.
As I stated earlier, all that we know for certain is that your server was attacked with a ~5Gbps DoS attack, it was sustained for an hour and it occurred within 24 hours of your server delivery. Your IPs were not recently recycled from another cancellation -- they had been sitting unused for quite some time. It's very unlikely someone else was being targeted.
We have had several customers in the past who stressed tested their own server with a DoS attack and then complained afterwards post-suspension that they were simply "making sure they're server can handle a DoS attack because [they] get attacked sometimes." Whether that's the case here, I have no way to confirm that, but it seems likely given that the server was attacked within 24 hours of delivery.
Either way, the cause for the attack is not important. What's important is that your server does not continue to be a DDoS magnet.
so you just advertised to everyone that you'll kick out your customers if they get ddos attacked. wow. I sense more deals coming.
@mosquitoguy We have no problem removing DDoS magnets from our network and I'm more than happy for potential customers to know that. We do not want that type of clientele on our network.
However, that's not what happened here. taizi was hit with a DDoS attack and his service still remains online. It didn't even go offline during the attack, but he did experience some weird network issues while the mitigation was active.
So what this thread actually shows is:
For a dedicated server under $40 per month server, that is more than fair.
The IPs not being recently recycled, does not mean they have a clean history.
There are some bad actors and it's understandable to be defensive, but the customer gave you his money. Maybe give him the benefit of the doubt and be a bit more supportive; monitor the IP before issuing it to another unlucky person.
The IP address had not been in use for months and had never been attacked before. This means that there was virtually no possibility this his server was targeted by "mistaken identity". A case of "mistaken identity" is a laughably unlikely excuse to begin with. The IP address was turned on for this client and he was then DDoS attacked in under 24 hours. It doesn't require sophisticated powers of logic to deduce who attracted the DDoS attack.
I understand your perspective, but unfortunately you can't be optimistic and hopeful when managing a network of thousands of leased servers. When you host thousands of servers, particularly low-end budget servers, fighting back abuse, spam, fraud, etc is a daily non-stop battle. Any host here with a significant number of customers will tell you the same. Taking a no-nonsense approach to network abuse is the only way you can keep your network running smoothly. It would be a disservice to our other customers if we did anything but that. They deserve quality service.
That said, we actually have given this customer the benefit of the doubt -- that's why he's still on our network. Most hosts would have simply terminated him and washed their hands of the problem. However, if the problem recurs, then we'll re-evaluate.
do you sure? when I search my IP in riskiq, it shows Last Seen is 2022-06-22

then I go to shodan and search again, last seen time is 2022-06-19
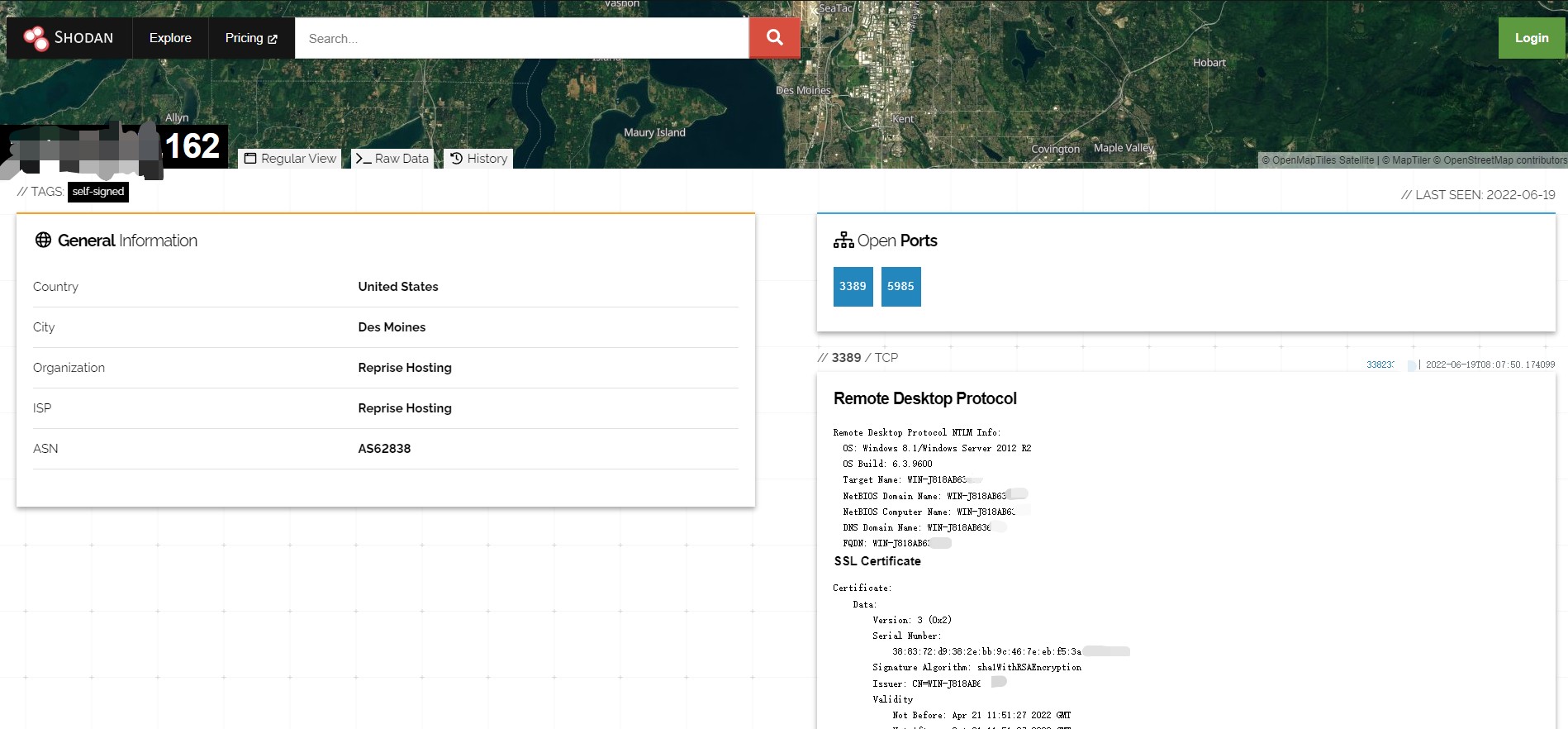
not been in use for months? maybe just for two weeks...😅
prerequisites:user not getting some random ddos