New on LowEndTalk? Please Register and read our Community Rules.
All new Registrations are manually reviewed and approved, so a short delay after registration may occur before your account becomes active.
All new Registrations are manually reviewed and approved, so a short delay after registration may occur before your account becomes active.
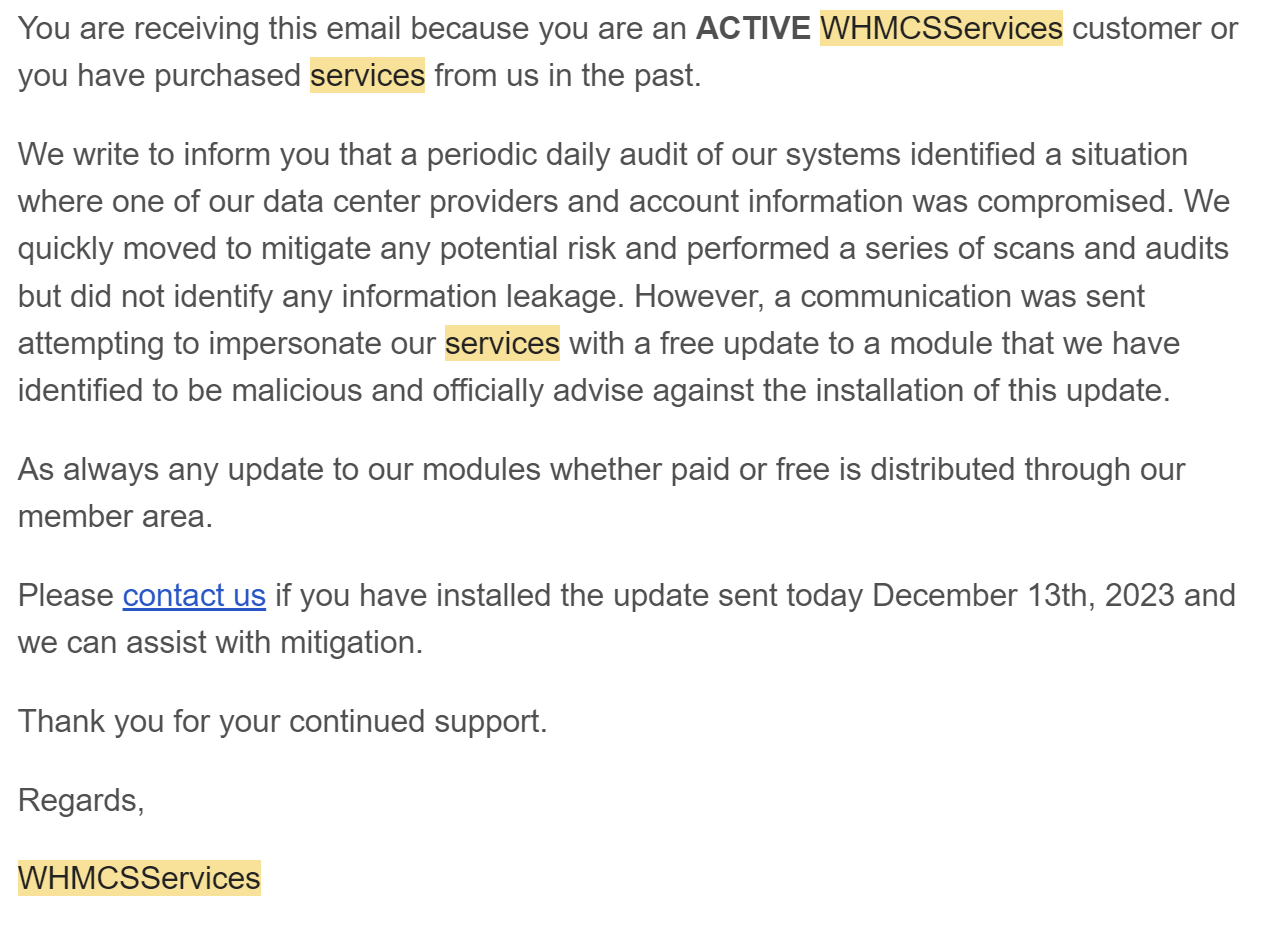
WHMCSServices (WHMCS Module Provider) Hacked
A popular WHMCS module provider, WHMCSServices, was recently hacked and modules were uploaded that contained malicious code. I thought of making this thread in private, but I think more people should be aware of this because some people were not sent emails about this (along with the fact that they may have not been fully transparent or descriptive about this) and there are a lot of hosting providers that probably use third-party WHMCS modules.
Thanked by 1thane

















Comments
I received something similar from cloudie as well, looks like they got compromised as well.
Received one from Mongodb as well, looks like there are more to come!

It is really odd that they were on the same date, but I don’t think they (MongoDB) use WHMCS so it might have just been a big coincidence.
I agree with that note, well what about Cloudie?
Yeah, looks like he was compromised too
Time for cloudie.rip?
Another host was impacted by this: https://status.quickhost.uk/incident/411384
I think this is especially interesting because it raises some concerns about using encoded WHMCS modules
Told you more to come, it's a kinda of trend to be followed up, when are you going to send these emails as well?
Who, us?
yeah aren't you using WHMCSservices as well?
Just so you are aware as no one has said so, Cloudie as already addressed this issue and has sorted it and is back online.
For clarification, here is the notification from Cloudie https://my.cloudie.sh/index.php?rp=/announcements/4/URGENT-SecurityorPayment-Invalidation-Notice-Action-Required.html
We removed their code a long time ago, before this hack took place. Even then, we’ve already audited their code and couldn’t find any backdoor or malicious files, and recently did another audit after the hack was announced. We’re still monitoring the situation, but given that the last time we had updated their module was >2 years ago, the fact that it was disabled/removed, and that we had audited the code multiple times, we are in the clear.
I am getting confused how the fuck from 'update to plugin' you are able to hijack communication between QuickHost and WHMCSServices resulting in FTP user, but I guess WHMCSServices is vague for a reason.
However I would just like to emphasize
Snapshot/backup using the same provider, even in different locations is NOT A BACKUP. Period.
Sounds convincing so far, now any NY deals upcoming?
More like time for whmcs.rip honestly
I wonder how many instances of WHMCS is affected right now, and what WHMCSSERVICES has to say bout this
Sounds like only those who upgraded their module from the fake source? Sounds like an email went out with an "update now" link and using that update is what allowed this?
Isn't it already dead right after it was bought by cPanel, Inc?
So far you hit the bullseye, it's the only reason viable right now.
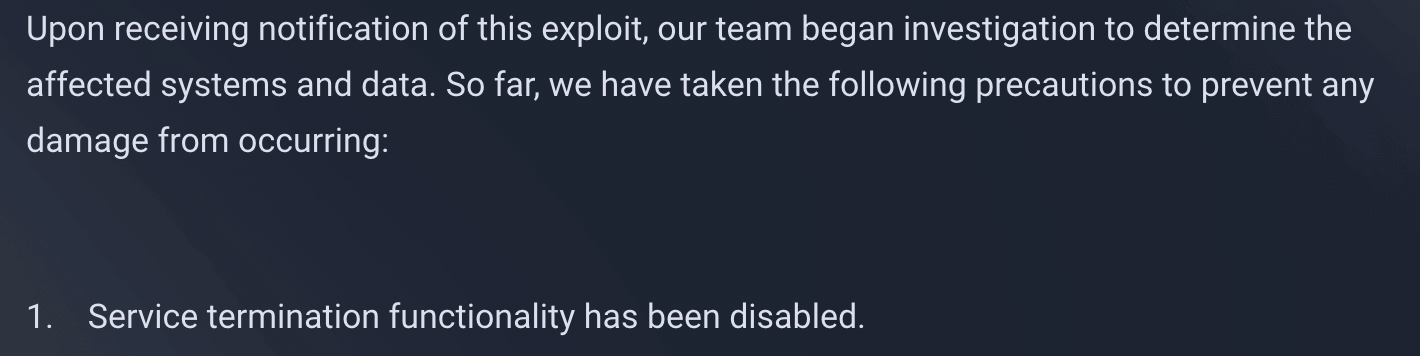
On the QuickHostUK status page, it looks like QuickHostUK provided FTP credentials to WHMCSServices to debug problems with their software, but instead a hacker accessed their systems with those FTP credentials to upload a malicious file. It looks to be more than just a phishing email like what happened with Swiftmodders. If there was a phishing email that got sent out, I didn’t get it.
I’m thinking that WHMCSServices may have gotten their email hacked, or even their full WHMCS instance, and maybe some compromised modules got sent to some hosting providers as an update. It’s unclear at the moment.
I don't believe you, share a link to the data.
lol
That it's cause why we don't usage any module on our WHMCS platform , and we preferred to make manual things , VPS delivery or other similar things...
Regards
this reminds me of a thread at LET something like "whats in WHCMS which blesta/hostbill lacks"
i guess its answer could well be found in this thread
And that is why you are up 18h of 24. or are you just feeding the bats in the cave all day?
Remember me writing WTF man, you have public IP on the nodes ? Wait for a proxmox exploit, that will be fun fun fun.
these things happen, so just sit tight.
Are you now threatening a kid to destroy him? not cool man!
ha ha ha, lol, from all, I think I am the last to threaten him, but he is young, he did not see enough shit, but he definitely will, he has a lot of time for that.
I am barely just guiding him. Reminds me of someone, a few decades ago
EDIT:
@Advin
Forgot to thank you for the fast info you provided.
Well, this manner of guiding is new to me, and believe me I didn't like it a bit.
I do not see any threat in the above, you might have understood something else, but we are derailing the thread by this, have something to say, write me.