New on LowEndTalk? Please Register and read our Community Rules.
All new Registrations are manually reviewed and approved, so a short delay after registration may occur before your account becomes active.
All new Registrations are manually reviewed and approved, so a short delay after registration may occur before your account becomes active.
A simple honeypot: ssh blasting password collection and real-time display on website
I found this post quite interesting:The machine is being blasted almost every second.
So, I wrote one myself, put it on the machine to collect other people's attack behaviors. And wrote a simple web page for display, which is equivalent to a simple honeypot application. It seems that the effect is really outstanding.
Website Demo
Screenshot
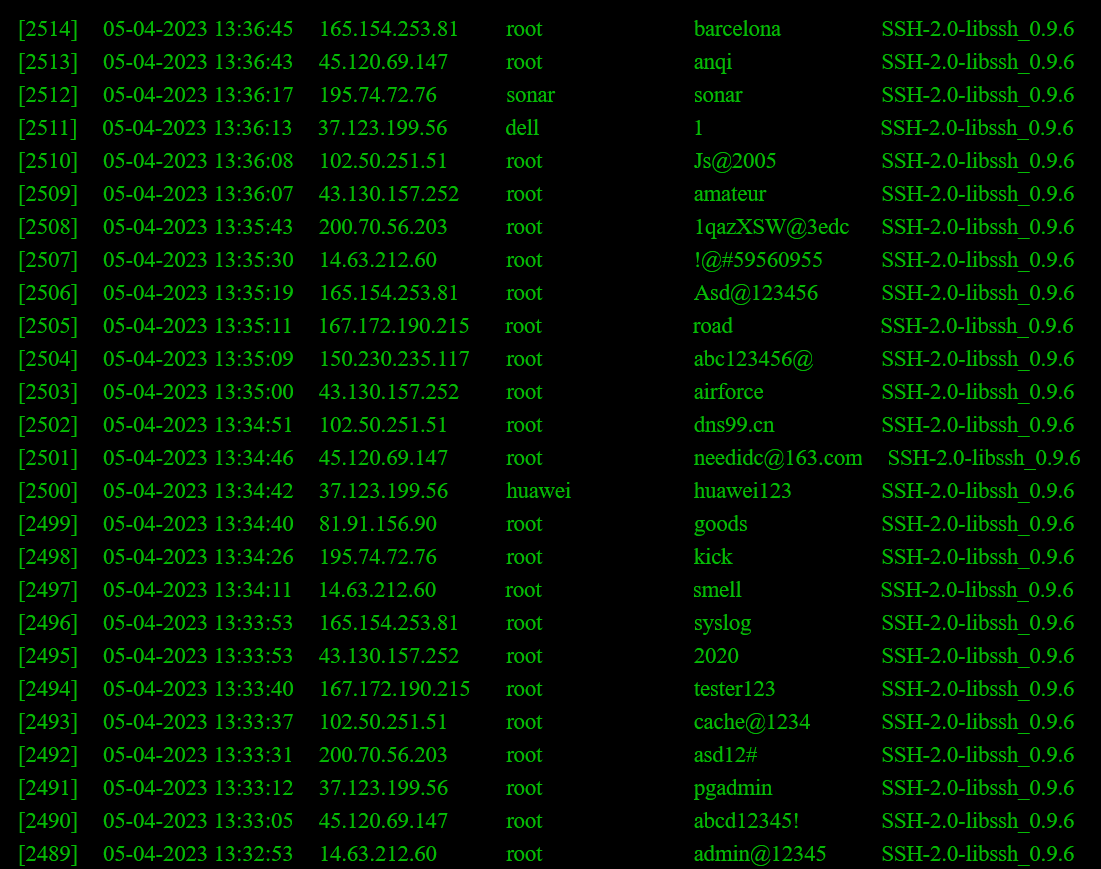

















Comments
How do you "write" such a thing?
Is it more than idling machine and exposing ssh on port 22 and then check auth.log?
Nope, ssh server itself doesn't log the usename and password by default.
So I write a fake ssh server, which only listen to 22 port and log the login attempts.
Neat website!
I'm kind of new to web development. How did you get that page to update in real-time?
I wonder if my servers are constantly being bombarded with SSH login attempts. I should check!
Impressive. Very nice. Let's see @fart 's honeypot.
Didn't know that changing nicks is possible here BTW. Can you explain what's up with that @angstrom ?
Didn't actually try it, but.....looks simple enough
Due to the fact that a billion dollar AI is incapable of quoting Bash variables properly, doing something as simple as
ssh '/*/*/*/*'@targeta few times will cause the machine that the script is running on to freeze, dump the entire filesystem into the public webpage and fill up the entire hard drive. Good job ChatGPT!I always knew you were smarter than a billion dollar AI!
That looks like backticks, which looks right if you quoted the thing you're talking about. Why wouldn't you quote an example matching your complaint? This is confusing.
Also, if something freezes on invalid input, they also don't know wtf they're doing, either.
I quoted exactly what it takes to crash the ChatGPT's script with catastrophic consequences.
It takes just this command:
It happens because in the following line generated by ChatGPT:
apart from using the ridiculously obsolete backtick notation for some reason, ChatGPT did not quote the $PAM_USER variable. When establishing the SSH connection, the variable is expanded to an attacker-supplied value (literally attacker-supplied - from somebody's who's brute forcing your box). In this case, the value is
/*/*/*/*- not POSIX-compliant but nonetheless valid username - which expands to a very large string containing every path on the filesystem, freezing the script and causing denial of service on the server.Further contributing to the catastrophe, that very large string is then appended to the log file and presented on a public webpage, spamming the hard disk until there is no more free space.
So basically 3 fuckups:
caused by a single line of code. That is assuming the code even works (it probably doesn't anyway).
Reference on bash quotes: https://mywiki.wooledge.org/Quotes
Reference on command injection (the general class of an attack I've just described): https://owasp.org/www-community/attacks/Command_Injection
Any bets on the first big company to blindly run untested ChatGPT code on their prod servers?
I don’t understand why someone will try it on chatgpt and post it again here, what is the point you are trying to make?
Yes in the near future chatgpt will be able to do anything its a tool but the idea and the creativity its from us humans who made this tools
My feeling is that it would happen without authorization at a company with poor software development processes and poor configuration management. I imagine a lazy engineer adding it to their code.
If I were to bet on a company where that could happen sooner than later, I nominate Twitter.
Why not just use fail2ban? That's what I use to create my blacklist.
This is already happening on a massive scale in every company that uses IT outsourcing. It's no coincidence that India is the largest non-US visitor demographic of openai.com.
Oh there's no doubt it's happening, I should have phrased the question a bit better. What I should have asked was what company is going to have a catastrophic failure because they ran random code from "AI" on their prod servers. It's inevitable but I'd sure be curious to see which one is going to bite the dust first.
maybe make all the failed login attempt IPs publicly available for download so people can add to their firewall?
Remember the stories about well-compensated engineers who would hire someone in a another country to do their work? They would pocket the difference as "profit" as well as not actually working. The ones in the news were doing stuff like giving their corporate remote access to the foreign worker, which gets noticed by the network security people, and other dumb behaviors like that.
I think you are much more likely to see AI-generated code "snuck in" by lazy developers. They will get caught when a bug is uncovered and then they can't explain their own code to their boss, their coworkers, or those who found the bug.
Then they use ChatGPT to make up an excuse. The circle is complete.
Although not exactly the same, check my signature for the list of IP addresses that are scanning the Internet for no reason.
Exactly my thought
provide direct links, no one wants to download a file manually to add ips to blocklists, a static url endpoint would be nice
I'm disappointing ChatGPT uses backticks which have been passé in shell code for...oh, I don't know, maybe 20 years.
I just use a custom
blacklist.confaction file to create the actual blacklist. Fail2ban does everything else for you. Been doing it this way for years. I don't see any reason to create custom scripts to parse and filter log files when you can have fail2ban do all of that for you.I've had ChatGPT make a few bash scripts for me and so far they have all worked perfectly first try. It didn't use backticks but maybe that's a
shthing. I only use bash.