New on LowEndTalk? Please Register and read our Community Rules.
All new Registrations are manually reviewed and approved, so a short delay after registration may occur before your account becomes active.
All new Registrations are manually reviewed and approved, so a short delay after registration may occur before your account becomes active.
















Comments
Don't disrespect your family.
Thank you, we have doubled your bandwidth.
It all begins with "legal" port scans.
Congrats on your first post
@yoursunny provides dedicated servers with 10kbps traffic located in Antarctica and everything is legal in Antarctica
Do ANY providers actually prevent port scans? I've certainly not come across one - most/all don't give a crap about port scanning neighbours, even when reported, never mind outbound scans.
How do you suppose provider should reliably monitor such behaviour? They only can block certain ports, but active monitoring of unmaged server is not viable.
So, when port scan happens, abuse report is received and provider reacts or not.
Digitalocean has some massive ces pool of port scanners.
oh and dont forget about the brute forcers
@LTniger The cess pool of port scanners extends much wider than that, Hetzner, Contabo, OVH, ColonCrossing, PonyTel, Clouvider, you name it!
Active monitoring is not a manual process; it should be trivial to detect numerous (short interval) outbound port scans from a specific IP and null route, until the f'ker explains themselves. At it's simplest, look how many of your network neighbours are needlessly sending broadcast packets.
It's not a question of blocking specific ports, it's the range of ports within a small timespan. The readily and freely available CSF easily tracks inbound packets from a single address. You can't tell me that something similar isn't available at switch/router level for packets that traverse networks.
Run a "dmesg" a couple of times, for just one minute and see just how many inbound blocks come from the same source. Goes off to block censys-scanner.com ..
The capabilities are there, it's purely a lack of willingness to tackle the issue - much like illegal (in the UK) telephone scam calls.
Hello,
We do offer port scans but you can only scan up to 65.536 IPs per day.
If thats okay for you, please reach out via private message.
Thanks.
They do autonull if they detect outgoing scans, AFAIK
They can certainly detect one on-going if they look for it. I suspect some will use active port scanning as a proxy indicator of malicious activity, but will only actually look if such other activity is detected or reported to them.
I'm not sure how you would go about detecting them at the DC level without getting a bunch of false positives to manage.
Managed switches for unmanaged servers.
At least for VMs, you can monitor traffic on each port and mitigate accordingly (e.g. rate limiting to IPs outside normally accessed ones until further investigation).
got your back Jack, bitches be crazy!
Well, as an indicator, I did have a blanket ban on all Hetzner (published) IPs but unfortunately some services use them for updates (Let's Encrypt, hetrixtools or something like that.)
Linode or DO. Some companies use their network to do unauthorized port scanning (they say it’s for security but who knows). Those scanners have been there for quite some years so I guess it’s fine as long as no abuse mails are received.
My position has always been that port scans for white hat reasons are fine and acceptable, and people getting pissed off because they don't know how to tune CSF to not email them about every little thing that doesn't matter is their own problem (and these are ALWAYS the people mad about it).
Researchers outing people for public facing MongoDB was a great example of a problem that was publicized based on port scanning before everyone vulnerable had been taken advantage of. I love efforts like that and the stats they provide. When I was at DO we were able to save thousands of customers from a problem we didn't know they had, because someone port scanned.
If you don't want people to know the port is open, don't leave it open. If you don't know what's open, you're not in a strong place to dictate how others define security. If you know you're secure, stand there with your dick out and let everyone admire it.
It's the overhead. Most people work their switches and routers to the bone. Doubling up on the hardware to do the job just isn't worth it financially for most. The demand is somewhere around one customer out of hundreds of thousands, and they're typically worth a max of $15/m revenue.
I'm more upset that the strechoid unidentified brute-forcer is still operating on DO, with no working opt out page, from all over DO space so I can't do anything other than block all of DO, and they're hitting my small vm's with 100k pps from multiple countries. I know the port is open, that doesn't mean you make 10GB worth of access.log and auth.log for no fucking reason >:[
VPN provider, thousands of accounts under different identities and seeming to be from different locations, white hat organization with their blessing. Likely one of those.
It's easy to think you'd put a stop to it right away in their shoes, but having been there... the reality of what malicious people do and how far they'll push you is more than most people sign up for.
In my eyes there is a big difference between automated port scanning and automated pen testing...
OP did say "to authorized IPs"... Maybe he is running a security evaluation service.
If he was really sketchy wouldn't be just say nothing and buy a cheap vps?
He is sketchy enough to ask such services on LET.
There are exactly 4 common reasons for portscanning.
The fact that OP asks for automated internet-wide scanning, we can safely assume that he either wants to do 3. or 4.
All but (1) needs to be blocked/culled, IMHO.
This, though logrotate at a 1000th of the size.
How many 'rogue' packets does it take to saturate the switch/router? (rhetorical) If the port scanning b'stards were stopped then the switches/routers would have far less traffic in the 1st place. Tackle at source.
Just like when storage was limited, there was a time where network overhead was reduced to a minimum (eg. high cost low bandwidth leased lines). Now nobody cares and NICs/servers just have to deal with the overheads of processing unwarranted traffic. :-\
Most port scans I've detected come from the following nodes:
1. compromised, malware-infected systems, which are the asymptomatic carriers of malware;
2. security researchers or cybersecurity vendors;
3. TOR exit nodes;
4. VPN servers.
Connections from all but (2) are malicious in nature. Not all connection attempts from (2) are innocent. Some cybersecurity vendors allowed their customers to initiate a scan against a third party's VPS without checking IP ownership first.
To reduce port scans, we have to reduce malware-infected systems, which means detecting and reporting them.
2800+ zombies detected from port scans in half an hour.
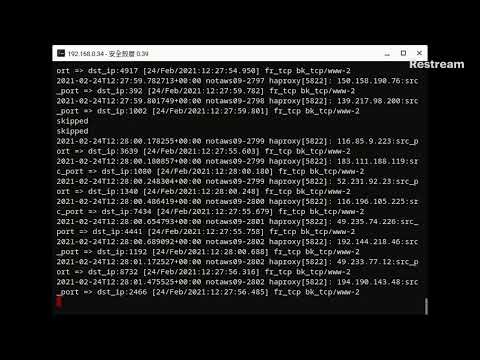
Really? auditing your self?
You don't need a port scanner to check your own ports tho.
The CCC agrees: https://translate.google.com/translate?sl=de&tl=en&u=https://koeln.ccc.de/ablage/portscan-policy.xml
Me too.
But I can also understand hosters who see it differently. Like cops, they deal with condensed shit every day. I bet that impacts someones opinions.