All new Registrations are manually reviewed and approved, so a short delay after registration may occur before your account becomes active.
Install vDDoS Proxy to AntiDDOS, DOS, SYN Flood, HTTP Floods attack...
How to install vDDoS Protection - Reverse Proxy Layer 7 Firewall Filter Mitigate DOS, DDOS, SYN Floods, or HTTP Floods attack
What is vDDoS Protection?
vDDoS Protection is free software to provide a Reverse Proxy Server HTTP(S) protocols. It act as a Layer 7 Firewall Filter & Mitigate DOS, DDOS, SYN Floods, or HTTP Floods attack to protect your website.
Features:
-Reverse Proxy
-DDoS Protection
-Robot Mitigator
-HTTP challenge/response
-reCaptcha Robot challenge
-HTTP Denial of Service tools
-Cookie challenge/response
-Block/Allow Country Code You Want (Status 403)
-Limit the request connection coming from a single IP address (Status 503)
-CDN Support (CloudFlare, Incapsula...)
-Whitelist for Botsearch (SEO Support, Allow Botsearch: Google, Alexa, Bing, Yahoo, Yandex, Facebook...)
How it work?
vDDoS Protection is Nginx bundled with module HTTP/2; GeoIP; Limit Req, Testcookie; reCaptcha processor... Working like CloudFlare, but vDDoS is software help you build your own System Firewall.
If your site does not use protection service: (accept all queries)
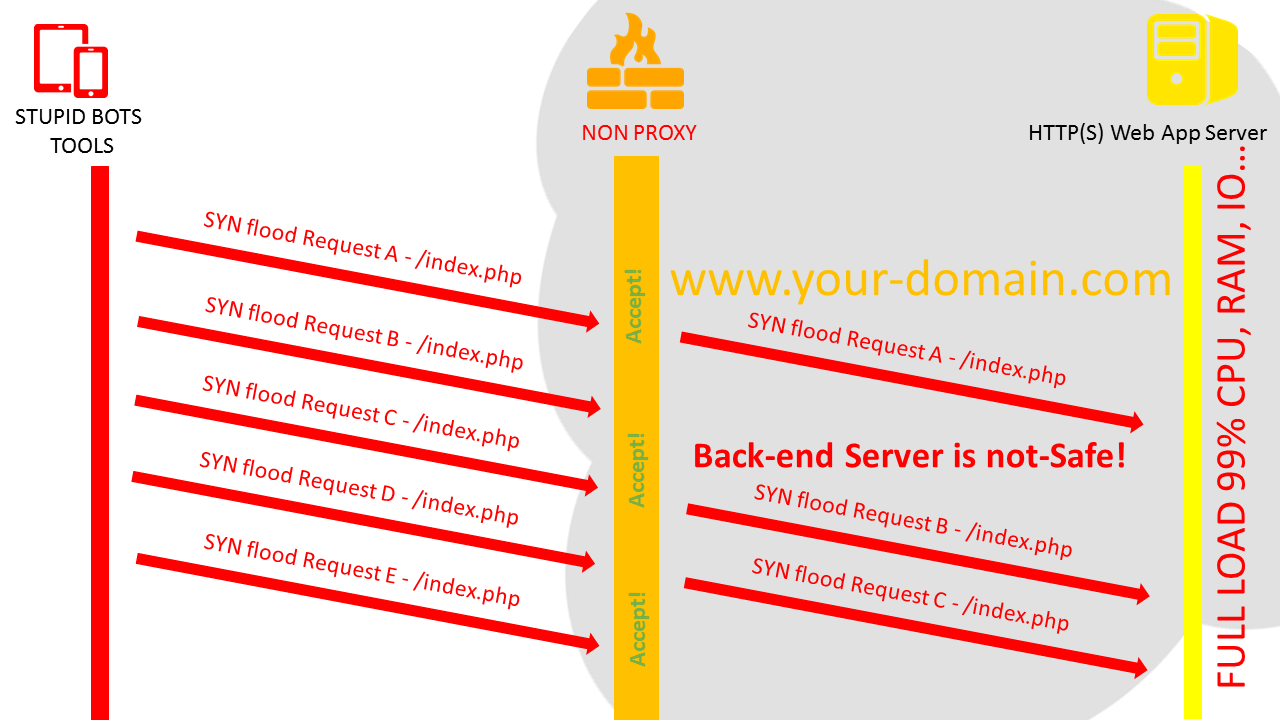
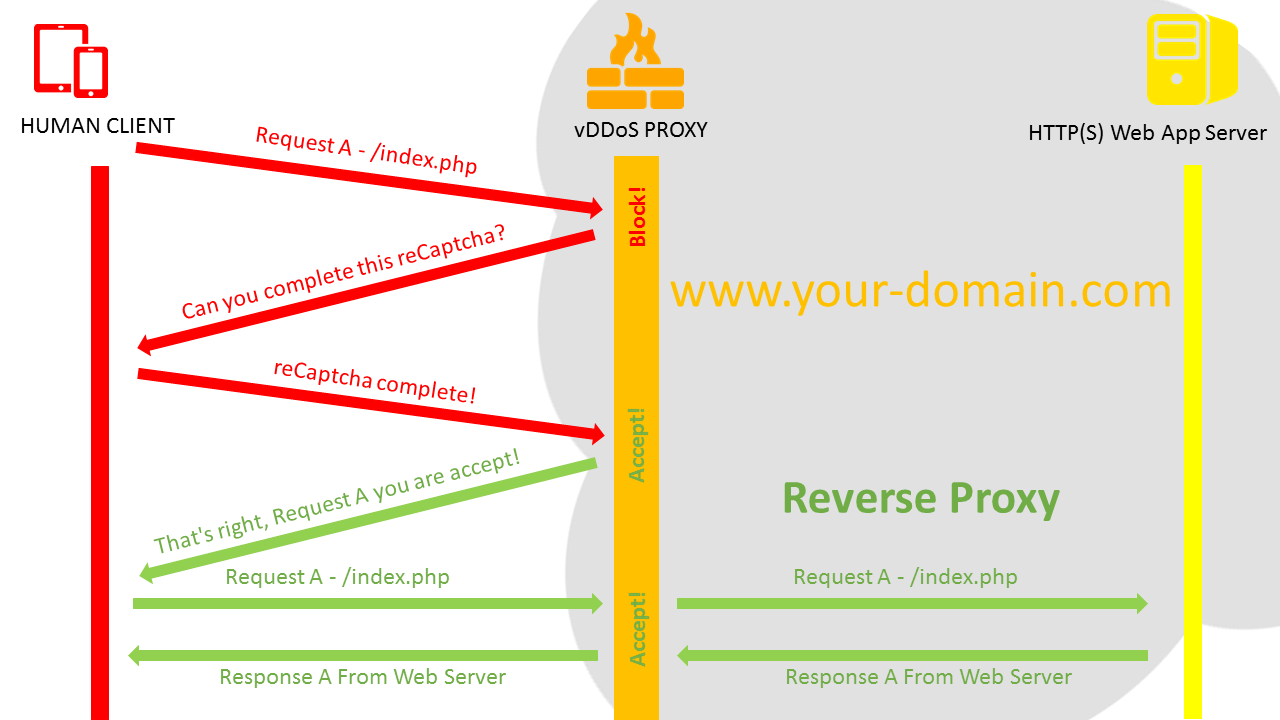
If your site uses protection service: (challenge all queries)
-Human queries:

-Bad Bots queries:


How to install vDDoS?
-vDDoS Protection only support CentOS Server 5/6/7 x86_64 (http://centos.org) & CloudLinux Server 5/6/7 x86_64 (http://cloudlinux.com)
-Please go to Homepage and download vDDoS Protection version working on your system (https://github.com/duy13/vDDoS-Protection)
-vDDoS Protection should be installed before installing other things (cPanel, VestaCP, LAMP, LEMP...)
yum -y install epel-release
yum -y install curl wget gc gcc gcc-c++ pcre-devel zlib-devel make wget openssl-devel libxml2-devel libxslt-devel gd-devel perl-ExtUtils-Embed GeoIP-devel gperftools gperftools-devel libatomic_ops-devel perl-ExtUtils-Embed gcc automake autoconf apr-util-devel gc gcc gcc-c++ pcre-devel zlib-devel make wget openssl-devel libxml2-devel libxslt-devel gd-devel perl-ExtUtils-Embed GeoIP-devel gperftools gperftools-devel libatomic_ops-devel perl-ExtUtils-Embed
Example: my system is CentOS 7 x86_64 install vDDoS 1.10.1 Version (only need wget a file vddos-1.10.1-centos7):
curl -L https://github.com/duy13/vDDoS-Protection/raw/master/vddos-1.10.1-centos7 -o /usr/bin/vddos
chmod 700 /usr/bin/vddos
/usr/bin/vddos help
/usr/bin/vddos setup
(This installation takes about 15 minutes or more)
vDDoS Command Line?
Welcome to vDDoS, a HTTP(S) DDoS Protection Reverse Proxy. Thank you for using!
Command Line Usage:
vddos setup :installing vDDoS service for the first time into /vddos
vddos start :start vDDoS service
vddos stop :stop vDDoS service
vddos restart :restart vDDoS service
vddos autostart :auto-start vDDoS services on boot
vddos attack :create a DDoS attacks to HTTP target (in 30 min)
vddos stopattack :stop "vddos attack" command
vddos help :display this help
Please sure download vDDoS source from: vddos.voduy.com
How to use vDDoS protect your website?
Please edit your website.conf file in /vddos/conf.d
Example Edit my website.conf:
# nano /vddos/conf.d/website.conf
# Website Listen Backend Cache Security SSL-Prikey SSL-CRTkey
default http://0.0.0.0:80 http://127.0.0.1:8080 no 200 no no
your-domain.com http://0.0.0.0:80 http://127.0.0.1:8080 no 200 no no
default https://0.0.0.0:443 https://127.0.0.1:8443 no 307 /vddos/ssl/your-domain.com.pri /vddos/ssl/your-domain.com.crt
your-domain.com https://0.0.0.0:443 https://127.0.0.1:8443 no 307 /vddos/ssl/your-domain.com.pri /vddos/ssl/your-domain.com.crt
your-domain.com https://0.0.0.0:4343 https://103.28.249.200:443 yes click /vddos/ssl/your-domain.com.pri /vddos/ssl/your-domain.com.crt
"your-domain.com" is my site on my Apache backend http://127.0.0.1:8080 want to be Protection by vDDoS
"default" is option for All remaining sites
/vddos/ssl/your-domain.com.pri is SSL Private key my website
/vddos/ssl/your-domain.com.crt is SSL Public key my website
Cache:
variable: no, yes (Sets proxy cache website on vDDoS)
Security:
variable: no, 307, 200, click, 5s, high, captcha (Sets a valid for Security Level Protection)
Note Security Level: no < 307 < 200 < click < 5s < high < captcha
Restart vDDoS after saving:
# vddos restart
Set Real IP traffic from Proxy or CDN:
Please edit file cdn-ip.conf
# nano /vddos/conf.d/cdn-ip.conf
# Cloudflare
set_real_ip_from 103.21.244.0/22;
...
Deny Country or IP:
Please edit file blacklist-countrycode.conf
#nano /vddos/conf.d/blacklist-countrycode.conf
geoip_country /usr/share/GeoIP/GeoIP.dat;
map $geoip_country_code $allowed_country {
default yes;
US yes;
CN no;
}
deny 1.1.1.1;
Allow your IP Address do not need protection & challenge:
Please edit file whitelist-botsearch.conf
# nano /vddos/conf.d/whitelist-botsearch.conf
#Alexa Bot IP Addresses
204.236.235.245; 75.101.186.145;
...
Use Mode reCaptcha:
Please edit file recaptcha-secretkey.conf & recaptcha-sitekey.conf
# nano /vddos/conf.d/recaptcha-sitekey.conf
# Website reCaptcha-sitekey (View KEY in https://www.google.com/recaptcha/admin#list)
your-domain.com 6Lcr6QkUAAAAAxxxxxxxxxxxxxxxxxxxxxxxxxxx
...
# nano /vddos/conf.d/recaptcha-secretkey.conf
DEBUG=False
RE_SECRETS = { 'your-domain.com': '6Lcr6QkUAAAAxxxxxxxxxxxxxxxxxxxxxxxxxxx',
'your-domain.org': '6LcKngoUAAAAxxxxxxxxxxxxxxxxxxxxxxxxxxx' }
(Go to https://www.google.com/recaptcha/admin#list and get your key for vDDoS)
Recommend?
-Recommend You use vDDoS with CloudFlare Free/Pro (hide your website real IP Address)
(CloudFlare is Mitigate Firewall Layer 3-4)
(vDDoS Protection is Mitigate Firewall Layer 7)
-Download vDDoS Protection packages from vDDoS HomePages
-Use this soft only for testing or demo attack!
vDDoS Protection is Simple like that!
















Comments
interesting
which branch of nginx is this based on ? 1.10 or 1.11 mainline ? how often will it be updated following nginx releases ?
your github readme is telling people to download and execute a random binary as root
as far as i can tell the only thing is you compile nginx-testcookie and apparently also ship an outdated version of openssl?
My first instinct was spam, but when I read it... I'm 50/50 on it now.
My suggestion would to actually host a package repo, then add it to the yum repo config, and install from there. It'd probably make it a lot easier to get updates of the software if you did.
A guide for CentOS 7: http://www.tecmint.com/setup-yum-repository-in-centos-7/
Also another is that you might want to use sudo for commands (this will allow the script to run under other users).
Seems pretty interesting.
Habe you tested how many concurrent users a 1gb ram vps can handle with this? Given each stream uses 20-30kb
Seems pretty interesting indeed, but shouldn't this be fully editable then the user can compile it by himself?
thanks.
Well, considering how effective the software is, I'd say 80 spam 20 not spam.
Synflood is Layer4 which has nothing to do with Layer7 (Application Layer). Your modified nginx will be useless for every real synflood, as it targets the network stack.
Thank you for comment! OK, to me, work against DDoS:
vDDoS just one thing is definitely for you: if that attack tools can't pass challenge => Your Back-end Server is Safe
If you don't have a filter:
Thanks for your comment! At the time I started writing this tool, stable version of nginx is 1.10.1 and Nginx 1.10.1 used default openssl on centos (it's very very outdated version of openssl) so I get the latest version of openssl at that time, openssl-1.0.2h because it helps nginx supports HTTP/2 on Chrome Browser. Just reinstall version openssl that people want after you install vDDoS.
Hi! I wrote this tool is to be used for my servers and my customers, I have no other plans for it at all, just wanted to share them with anyone who wants to use. Please use it only for demo & testing
Sorry everyone because my english is bad, somebody if interested please help me correct my grammar!
i will try it on my DNS server.
Becaful, Please use it only for demo & testing. And vDDoS is HTTP(S) Reverse Proxy it can't Proxy for DNS protocol UDP/53
Do you plan to release a open-source variant instead of binary form?
Thanks for your interest! vDDoS is just a shell script file auto install and config nginx + module that i want. I am only a system administrator And I am not confident about my ability to program so I did it out binary coding to protect my servers, and my customers servers.
Yes! Of course I want to release an open source version in the future, but now? I'm not sure it safe for my customers.
I just wanted to give an idea like that, someone good programmer should create a similar product, but more professional. And I'll take it on to use ^^
Ask your contacts, I would like to discuss some of the details
Skype: voduy13
I think you have got it badly wrong. For a start openssl isn't a smart choice and even less so when nailing users of your stuff down to any given version.
Moreover it seems you haven't properly understood what a DDOS is and how it works. Also your explanation
suggests a rather strange (no-)understanding of how DDOS work.
Sorry, I would like to ask a detailed explanation of the website.conf configuration file
I configure the website.conf file, but the domain name is Apache information page, not [178.32.100. **:50478] page content
Do I understand the error?
Backend entry is not [need to reverse the proxy ip: port]?
How can i be configured correctly?
PS:
I [centos-512mb-sgp2-02] VPS has installed LAMP (LAMP.sh a key install package) and vDDoS Proxy
[178.32.100. **: 50478] is another VPS
As i see:
Why "Server: Apache"? Are you sure vDDOS running on port 80?
netstat -lntup|grep 80[root@centos-512mb-sgp2-02 ~]# netstat -lntup|grep 80tcp 0 0 127.0.0.1:10101 0.0.0.0:* LISTEN 5280/python2.7
tcp6 0 0 :::80 :::* LISTEN 14487/httpd
centos-512mb-sgp2-02 VPS Installed LAMP and vDDoS Proxy
Is it only installed vDDoS Proxy, in order to normal use?
[root@centos-512mb-sgp3-03 ~]# netstat -lntup|grep 80tcp 0 0 0.0.0.0:80 0.0.0.0:* LISTEN 3501/nginx: master
centos-512mb-sgp3-03 VPS Install only vDDoS Proxy
# Website Listen Backend Cache Security SSL-Prikey SSL-CRTkey
test9.loli.mn http://0.0.0.0:80 http://178.32.100.**:50478 no 200 no no
centos-512mb-sgp3-03 VPS Website.conf configuration file ↑
But the test9.loli.mn page content is 403
Curl -I test9.loli.mn is shown below
[root@centos-512mb-sgp4-04 ~]# curl -I test9.loli.mnHTTP/1.1 200 OK
Server: nginx-V-ddos
Date: Mon, 10 Apr 2017 17:43:42 GMT
Content-Type: text/html
Content-Length: 142
Connection: keep-alive
Keep-Alive: timeout=60
Expires: Thu, 01 Jan 1970 00:00:01 GMT
Cache-Control: no-cache
Also said that only must install vDDoS Proxy, in order to normal use?
Can not install other LAMP?
But only install vDDoS Proxy, but is 403 ... ...
Deny Country or IP:
Please edit file blacklist-countrycode.conf
That my example deny a country:
Please remove CN no;. PM my skype for Such support, thanks!
Has been successful, very grateful!
You are welcome!
DEMO PART 2 TUTORIAL HERE: https://www.lowendtalk.com/discussion/102642 for those who don't know...
In addition, I would like to ask
If you want to use SSL for domain names
Backend (source station) IP, must also be SSL?
Because of my own test time
Backend (source station) IP non-SSL, the site is not complete, the lack of pictures, CSS and other content, only text
Backend (source station) IP is SSL, the site appears normal
Im sure Backend (source station) IP non-SSL -> that mode like CloudFlare Flexible SSL
Backend (source station) IP is SSL -> Full SSL mode on CloudFlare
Stay Classy!
Not open source all content? Thanks.
How to use flexible ssl?
Will websockets works?
source code at https://github.com/duy13/vDDoS-Protection/raw/master/vddos-1.10.2.tar.gz
It's based on Nginx v1.10.2 and testcookie (https://github.com/kyprizel/testcookie-nginx-module) and testcookie-recaptcha-processor.
I think you should build from source (nginx.org + github) instead run from binary file.